#How to Add IP Address in Windows Firewall
Explore tagged Tumblr posts
Text
Boost your Windows VPS server security by configuring a Windows firewall to allow only trusted IP addresses access to specific ports with our guide.
#How to configure the Windows Firewall to allow only specific IP Address#How do I allow only certain IP Address in Windows Firewall?#How to Add IP Address in Windows Firewall
0 notes
Text
5 Security Tips for Accountants Who Work Online

Like any other digital profession, accounting work is also prone to security threats. You never know who’s watching when you work online—whether you’re reviewing payroll, filing taxes, or accessing bank records.
The tools you use are powerful, but they’re not bulletproof. Even a single careless login, outdated system, or unsecured password can open the door to data theft.
If you manage accounts online, security isn’t a nice-to-have—it’s a responsibility. So, let us give you 5 tips to help you keep your work, your clients, and your reputation safe.
Why Does Security Matter for Accountants Who Work Online?
If you’re an accountant, you must know how to handle more than mere calculations. You have to manage confidential records—bank details, tax filings, payrolls, and business ledgers. Right? That data is valuable. If stolen, it can lead to identity theft, fraud, or financial loss.
It’s also very clear that cybercriminals often target small firms, freelancers, and even individual accountants. They assume basic security mistakes—like weak passwords or unchecked access—will let them in.
See, online tools make work faster, but every connection you open adds risk. One exposed account can compromise dozens of client files. One leaked password can open access to banking platforms. Most breaches don’t happen through high-level hacking. They happen through ignored updates, reused passwords, and careless clicks.
So, security matters because you work with trust. If clients feel exposed, they walk away. If data leaks, your reputation suffers—even if recovery is possible.
A secure system shows control. It proves that your practice is professional, reliable, and ready to grow in the digital age.
What Security Tips Should Accountants Follow?
Use Two-Factor Authentication on Every Account You Log Into Passwords are easy to steal. Phishing, leaked databases, or weak combinations can expose your login in seconds. Two-factor authentication (2FA) adds one more step that attackers cannot bypass.
When 2FA is active, logging in requires two things:
Your password
A second code sent to your phone or generated by an app
Even if someone knows your password, they cannot get in without that second code.
You should turn on 2FA for all work accounts:
Email
Cloud storage
Accounting platforms
Bank logins
The majority of tools support 2FA through SMS or apps like Google Authenticator. It takes only a few minutes to enable it, and if you ignore it, you’ll leave the door open to cybersecurity threats.
Update Your Software Regularly to Close Security Gaps
Outdated software becomes an easy target. Hackers look for known flaws in older versions of apps, operating systems, and plugins. Sometimes, when a company discovers a vulnerability, it releases a patch. If you delay the update, you stay exposed.
You should always keep the following up to date:
Operating systems (Windows, macOS)
Accounting software (QuickBooks, Xero)
Browsers and extensions
Antivirus and firewall tools
See, attacks don’t always break new ground. They hit users who skip updates. So, staying current blocks the attacks before they start.
Check Your IP Location History to Detect Suspicious Logins
Every time you log into a service, your device uses an IP address. That IP shows your IP location—the city, region, or country of the request.
You can review that login history on many platforms:
Google and Microsoft accounts
Cloud storage dashboards
Some accounting software with activity logs
If you see a login from a place you’ve never visited, it signals a security breach. Even if the login was successful, you should change your password and enable alerts.
Track your IP location weekly. That habit helps you catch threats early, especially when your credentials are reused without your knowledge.
Use a DNS Lookup Tool Before Trusting Unfamiliar Websites
Scam websites look real. Hackers copy bank portals, tax sites, or accounting dashboards to steal your login. The design may match, but the domain tells the truth.
You should run a DNS lookup before entering credentials on any unfamiliar link because it:
Verifies MX records to ensure client emails are deliverable.
Confirms SPF, DKIM, and DMARC records to prevent spoofing and phishing.
Checks A and AAAA records to validate server IPs for accounting software.
Identifies CNAME records to confirm safe redirects to client portals.
Detects NS records to confirm that domains use trusted name servers.
Spots missing or incorrect DNS entries that could block file sharing or logins.
Helps troubleshoot email issues, server downtimes, and domain misconfigurations.
If the domain was created recently or points to unknown servers, avoid it. Trust only domains linked to verified companies with clear records.
Store Your Passwords in a Secure Password Manager
Passwords stored in documents, emails, or notebooks can be stolen easily. Anyone with access to your device or inbox can find them.
You should use a password manager instead. It keeps all your logins in one encrypted vault. You only need to remember one strong master password.
See, a good password manager:
Encrypts your data locally
Syncs securely across devices
Fills in passwords without exposing them
Avoid browser-based storage without a vault. Choose a dedicated tool with zero-knowledge encryption and backup recovery options. That way, your credentials stay safe—even if your device doesn’t.
What Happens If You Ignore These Security Steps?
You put your clients—and your entire practice—at risk.
No two-factor authentication means anyone who guesses or steals your password can log into your cloud accounting software. They can access balance sheets, tax records, and payroll details without you knowing.
Skip software updates, and you leave your system open to known bugs. A ransomware attack can lock your entire client database, right before tax season.
Ignore your IP location logs, and you might miss a login from another country using your credentials. A hacker could change invoice numbers, redirect payments, or silently download reports while you work on something else. Or merely trust a fake login page without a DNS lookup, and you could enter your bank credentials into a cloned website. Funds disappear. So do transaction records.
Keep client passwords saved in a spreadsheet or email draft, and a single device theft means multiple client accounts get exposed at once. One client might forgive that. Most won’t.
Each mistake alone creates damage. Ignore all five, and you remove every layer of protection. You won’t just lose data—you’ll lose trust, contracts, and possibly your license to operate.
Accountants work with private, high-value data. That’s why online security isn’t optional. It’s basically part of the job.
Bottom Line
Don’t invite risk by skipping 2FA, ignoring updates, overlooking IP logs, trusting unverified sites, or saving passwords insecurely. As an accountant working online, your safety depends on consistency. The smartest tip? Treat security like part of your workflow—not an afterthought.
0 notes
Text
Step by Step Strategy: How to Plan Your Windows VPS Server

Setting up a Windows Virtual Mystery Server (VPS) can have every one of the reserves of being overwhelming, particularly in the event that you are new to the universe of servers and remote working with. However, with an accurate way of thinking, arranging your Windows VPS can clear and reward. This guide will walk you through each step, promising you have an absolutely significant and secure Windows VPS server near the end.
1. Picking The Right VPS Supplier
Before you begin arranging your Windows VPS, you really want to pick a dependable VPS supplier. Two or three trustworthy suppliers incorporate Amazon Web Services(AWS), Microsoft Sky blue, DigitalOcean, and Vultr. Parts to consider while picking a supplier include:
Regarding: Confirmation the expense obliges your money related game plan.
Assets: Check how much Pound, PC processor power, and circle space advanced.
Support: Mission for suppliers with searing client organization.
Locale: Select a server district that is near your vested party to confine inaction.
2. Laying Out Up Your Vps Record
Right when you've picked a supplier, you'll have to make a record. This commonly integrates:
Joining: Give your email address, make a secret word, and insist your record.
Picking A Strategy: Select a blueprint that settle your issues concerning assets and spending plan.
Segment: Add a part technique to help your record.
Just in the wake of laying out up your norm, you can continue to make your Windows VPS.
3. Sending Your Windows VPS
Sending a Windows VPS integrates a few key stages:
Select The Windows Working Structure Rendition: Pick the variety of Windows you need to introduce, for example, Windows Server 2016, 2019, or 2022.
Plan Server Particulars: Choose the central processor, Pulverize, and limit fundamentals.
Dispatch A Server Name: Give your VPS a phenomenal and illustrative name for fundamental ID.
Pick A Datacenter District: Select a locale that gives the best show to your necessities.
Survey And Convey: Study your plan and send your VPS.
Most suppliers will blueprint your server inside a few minutes, after which you will get an IP address and login capacities.
4. Band Together With Your Windows Vps
Exactly when your VPS is passed on, you want to associate with it. The most outstanding procedure for connecting with a Windows VPS is through Distant Work area Show (RDP):
Find The Ip Address: Find the IP address of your VPS from your supplier's control board.
Use Far Away Work Area Association: Open the Far off Work area Alliance application on your nearby Windows machine.
Enter the IP address of your VPS.
Click "Accomplice."
When provoked, enter the username and secret articulation given by your VPS supplier.
Once related, you will see the work area of your Windows VPS, and you can talk with it as you would with a nearby machine.
5. Starting Strategy
Upon your first login, there are several starting arrangement pushes toward guarantee your VPS is secure and prepared for use:
Update Windows
Run Windows Update: Affirmation your server has the most recent updates and fixes. Open the Beginning menu, go to Settings > Update and Security > Windows Update, and snap "Check for resuscitates."
Present Updates: Download and introduce each accessible update, then, restart your server whenever provoked.
Arrange Boss Record
Change Default Secret Word: Immediately change the default boss secret articulation to critical strong regions for a, one. Press Ctrl+Alt+Delete, select "Change a secret word," and follow the prompts.
Make Another Central Record: For added security, make another head record and tested individual the default one.
Open the Beginning menu, go to Settings > Records > Family and different clients.
Click "Add another person to this PC."
Follow the prompts to make another client account with authoritative differentiations.
Arrange Firewall
Windows Firewall: Affirmation Windows Firewall is empowered and coordinate any key norms to permit or deter express traffic.
Open the Beginning menu, type "Windows Protector Firewall," and press Enter.
Click "Turn Windows Protector Firewall on or off" and guarantee it's locked in for both private and public affiliations.
Inbound Principles: Add rules to permit traffic for unequivocal applications or associations if significant.
Click "Critical level settings."
Select "Inbound Standards" and add new guidelines as required.
6. Present Focal Programming
With your VPS got and coordinated, this second is the best an open door to introduce the thing you'll require:
Web Server
Web Data Associations (IIS): In the event that you mean to have objections, present IIS.
Open the Beginning menu, type "Server Regulator," and press Enter.
Click "Add occupations and parts."
Follow the wizard to introduce the Internet Server (IIS) work.
Information Base Server
SQL Server: For information base association, present Microsoft SQL Server.
Download the installer from the Microsoft page.
Run the installer and follow the game-plan wizard to introduce SQL Server and plan your information base settings.
Extra Programming
FTP Server: On the off chance that you really need record move limits, present a FTP server like FileZilla.
Control Board: Consider introducing a control board like Plesk or cPanel to truly deal with your server.
7. Setting Up Fortresses
Ordinary strongholds are urgent for information affirmation. Most VPS suppliers offer robotized support blueprints, however you can also set up manual fortresses:
Supplier Fortresses: Empower mechanized strongholds through your VPS supplier's control board.
Manual Fortresses: Utilize worked in Windows contraptions to make framework pictures and backing tremendous reports.
Open the Beginning menu, type "Backing settings," and press Enter.
Follow the prompts to set up a help plan and get what to back.
8. Seeing and Support
Standard seeing and upkeep guarantee your VPS moves along exactly as expected:
Taking Note
Asset Utilization: Screen PC processor, Smash, and plate use utilizing Assignment Chief or Execution Screen.
Security Logs: Dependably check security logs for any noteworthy turn of events.
Open the Beginning menu, type "Occasion Watcher," and press Enter.
Examine to Windows Logs > Security to survey logs.
Upkeep
Programming Updates: Consistently update familiar programming with guarantee you have the most recent security fixes and parts.
Circle Cleanup: Intermittently run Plate Cleanup to clear out pointless records and set free space.
Open the Beginning menu, type "Circle Cleanup," and press Enter.
Follow the prompts to tidy up your circle.
9. Getting Your VPS
Security is crucial for any server. Here are extra advances toward secure your VPS:
Draw in Affiliation Level Endorsement (NLA): Affirmation that imperatively affirmed clients can fan out RDP affiliations.
Open the Beginning menu, type "Framework," and press Enter.
Click "Far away settings" and check "Award affiliations just from PCs running Far off Work area with Affiliation Level Certification."
Present Antivirus Programming: Protect your server with antivirus programming like Windows Safeguard or a distant game-plan.
Standard Security Reviews: Unpredictably perform security overviews to perceive and coordinate inadequacies.
End
Arranging a Windows VPS Server consolidates several phases, from picking the right supplier to getting and remaining mindful of your server. By following this gradually helper, you can set up major areas of strength for a, and suitable Windows VPS custom fitted to your essentials. Whether you are working with regions, running applications, or overseeing information bases, a particularly arranged VPS can give the show and determined quality you genuinely care about.
0 notes
Text
what is vpn type
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is vpn type
Virtual Private Network Definition
A Virtual Private Network (VPN) is a secure and encrypted connection that allows users to access the internet privately and securely. VPNs create a private network from a public internet connection, enabling users to send and receive data as if their devices were directly connected to a private network. This technology adds a layer of security and privacy to both public and private networks, making it an essential tool for protecting sensitive information.
One of the key functions of a VPN is to mask the user's IP address and encrypt their data, making it difficult for third parties to track their online activities. By routing the internet connection through a remote server, VPNs provide anonymity and prevent cybercriminals, government agencies, ISPs, and other entities from monitoring or intercepting online communications.
Furthermore, VPNs are widely used by individuals and organizations to bypass internet censorship and geo-restrictions. Users can connect to servers in different locations around the world, allowing them to access region-locked content, websites, and services that may be restricted in their own country.
In summary, a Virtual Private Network is a powerful tool that enhances online security, privacy, and freedom. By encrypting internet traffic and hiding the user's IP address, VPNs enable users to browse the web anonymously and access restricted content without compromising their data. Whether for personal or business use, VPNs have become an indispensable solution for safeguarding online activities in an increasingly interconnected world.
Types of VPN Protocols
When it comes to securing your online activities and protecting your privacy, Virtual Private Networks (VPNs) are an essential tool. These networks encrypt your internet connection, shielding your data from prying eyes. However, not all VPNs are created equal, and understanding the different protocols they use can help you choose the right one for your needs. Here are some of the most common types of VPN protocols:
OpenVPN: This open-source protocol is highly versatile and widely used due to its strong security features and flexibility. It can run on various platforms and devices and is known for its reliability.
L2TP/IPsec (Layer 2 Tunneling Protocol/IP Security): L2TP/IPsec combines the best of both L2TP and IPsec protocols to provide a secure and stable connection. While it's generally considered secure, some users may experience slower speeds compared to other protocols.
IKEv2/IPsec (Internet Key Exchange version 2/IP Security): Known for its speed and stability, IKEv2/IPsec is often preferred for mobile devices due to its ability to quickly reconnect to the VPN after a connection interruption.
SSTP (Secure Socket Tunneling Protocol): Developed by Microsoft, SSTP provides high levels of security by using SSL/TLS encryption. It's primarily used on Windows devices and is known for its ability to bypass firewalls.
PPTP (Point-to-Point Tunneling Protocol): While once popular for its ease of setup and fast speeds, PPTP is now considered outdated and less secure compared to other protocols. It's best avoided if possible due to its vulnerabilities.
Choosing the right VPN protocol depends on your specific needs, including security, speed, and compatibility with your devices. By understanding the differences between these protocols, you can make an informed decision to ensure your online activities remain private and secure.
VPN Encryption Methods
VPN encryption methods are fundamental to understanding how Virtual Private Networks (VPNs) secure your online activities and data. Encryption plays a crucial role in ensuring that your sensitive information remains private and secure while it travels across the internet.
There are several encryption methods commonly used by VPN providers to safeguard your data:
AES (Advanced Encryption Standard): AES is widely regarded as one of the most secure encryption algorithms available today. It utilizes symmetric key encryption, where both the sender and the receiver use the same key to encrypt and decrypt data. AES comes in different key lengths, with 256-bit AES being the most secure and commonly used by VPNs.
OpenVPN: OpenVPN is an open-source VPN protocol known for its flexibility and strong security features. It can utilize various encryption algorithms, including AES, Camellia, and Blowfish, making it adaptable to different security needs.
IPsec (Internet Protocol Security): IPsec is a suite of protocols used to authenticate and encrypt IP packets in a VPN. It can operate in two modes: Transport mode, which encrypts only the data payload, and Tunnel mode, which encrypts the entire IP packet. IPsec commonly uses AES encryption for data confidentiality.
WireGuard: WireGuard is a relatively new VPN protocol known for its simplicity and efficiency. It implements modern cryptographic techniques, including Curve25519 for key exchange and ChaCha20 for encryption, providing strong security with minimal overhead.
When choosing a VPN service, it's essential to consider the encryption methods it employs. Look for providers that offer robust encryption, such as AES-256, and support secure protocols like OpenVPN or WireGuard. Additionally, ensure that the VPN service follows best practices for encryption implementation to maximize your online security and privacy.
Common VPN Applications
Virtual Private Networks (VPNs) have become increasingly popular tools for safeguarding online privacy and security. With cyber threats on the rise, VPN applications offer users a way to encrypt their internet connection and anonymize their online activities. Here are some common VPN applications widely used today:
ExpressVPN: Known for its fast speeds and strong encryption, ExpressVPN offers servers in numerous countries, allowing users to access geo-restricted content with ease. Its user-friendly interface and reliable performance make it a top choice for many.
NordVPN: Renowned for its robust security features, NordVPN utilizes military-grade encryption and offers specialized servers for tasks like streaming and torrenting. Its strict no-logs policy and user-friendly interface make it a favorite among privacy-conscious users.
Surfshark: Offering unlimited simultaneous connections, Surfshark is a budget-friendly option without compromising on security. With features like CleanWeb, which blocks ads and malware, Surfshark provides comprehensive protection for all devices.
CyberGhost: Ideal for beginners, CyberGhost offers easy-to-use apps and specialized servers optimized for various tasks. Its strong focus on privacy, including a strict no-logs policy and automatic kill switch, makes it a reliable choice for users seeking anonymity.
Private Internet Access (PIA): Known for its affordability and extensive server network, PIA offers robust security features like DNS leak protection and customizable encryption settings. Its commitment to user privacy and open-source software make it a popular choice among tech-savvy users.
These VPN applications vary in features and pricing, catering to different user needs and preferences. Whether you're concerned about protecting your online privacy, accessing geo-restricted content, or securing your connection on public Wi-Fi networks, there's a VPN application suited to your requirements. Before choosing a VPN, consider factors such as speed, security, server locations, and compatibility with your devices to ensure you find the best fit for your needs.
VPN Service Providers
Protect Your Online Privacy with VPN Service Providers
In an era where online privacy is increasingly under threat, Virtual Private Network (VPN) service providers have become essential tools for safeguarding your digital presence. VPNs offer a secure and encrypted connection between your device and the internet, ensuring that your data remains private and protected from prying eyes.
One of the primary benefits of using VPN service providers is the ability to mask your IP address. By routing your internet traffic through servers located in different countries, VPNs obscure your true location and make it appear as though you are accessing the internet from another location. This not only enhances your privacy but also allows you to bypass geographic restrictions and access content that may be blocked in your region.
Furthermore, VPNs add an extra layer of security when using public Wi-Fi networks. These networks are notoriously vulnerable to hacking and snooping, but with a VPN, your data is encrypted, making it nearly impossible for cybercriminals to intercept and decipher your communications.
Choosing the right VPN service provider is crucial for ensuring maximum security and reliability. Look for providers that offer strong encryption protocols, a strict no-logs policy, and a wide selection of server locations. Additionally, consider factors such as connection speed, customer support, and compatibility with multiple devices.
While there are many free VPN services available, it's important to exercise caution, as they may not offer the same level of security and privacy protection as paid providers. Investing in a reputable VPN service is a small price to pay for the peace of mind knowing that your online activities are shielded from surveillance and censorship.
In conclusion, VPN service providers play a vital role in protecting your online privacy and security. By encrypting your internet connection and masking your IP address, VPNs ensure that your personal data remains confidential and inaccessible to unauthorized third parties. When choosing a VPN provider, prioritize security, reliability, and compatibility to enjoy a safe and unrestricted online experience.
0 notes
Text
does vpn work for 2012 r2 servers
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn work for 2012 r2 servers
VPN connectivity for Windows Server 2012 R2
VPN connectivity for Windows Server 2012 R2 offers businesses and organizations a secure and efficient way to connect remote users or branch offices to their network resources. By leveraging Virtual Private Network (VPN) technology, Windows Server 2012 R2 enables administrators to establish encrypted connections over the internet, ensuring data confidentiality and integrity.
Setting up VPN connectivity on Windows Server 2012 R2 involves several steps to ensure a seamless and secure connection. Firstly, administrators need to install the Remote Access role through the Server Manager console. This role encompasses various features, including DirectAccess and VPN, which are essential for remote connectivity.
Once the Remote Access role is installed, administrators can configure VPN settings using the Routing and Remote Access console. They can choose between different VPN protocols such as PPTP, L2TP/IPsec, SSTP, or IKEv2, depending on their security and compatibility requirements. Each protocol offers distinct advantages in terms of performance and encryption strength.
After selecting the appropriate VPN protocol, administrators need to configure authentication methods to verify the identity of connecting users. Windows Server 2012 R2 supports various authentication protocols, including MS-CHAPv2, EAP-TLS, and RADIUS, allowing organizations to integrate with existing authentication infrastructures seamlessly.
Furthermore, administrators must configure network policies to define access permissions and enforce security settings for VPN connections. This includes specifying IP address assignment methods, encryption algorithms, and access control rules to ensure that only authorized users can access network resources.
Once the VPN configuration is complete, remote users can establish secure connections to the Windows Server 2012 R2 network using VPN client software. Whether employees are working from home or accessing resources from a remote location, VPN connectivity on Windows Server 2012 R2 provides a reliable and secure solution for remote access needs.
Network security for 2012 R2 servers
Network security for 2012 R2 servers is crucial to ensure the protection of sensitive data and maintain the integrity of the server environment. As technology evolves, so do security threats, making it essential to stay vigilant and implement robust security measures.
To enhance network security for 2012 R2 servers, organizations should follow best practices such as regularly updating operating systems and applications to patch vulnerabilities. Additionally, deploying firewalls and intrusion detection/prevention systems can help detect and mitigate potential threats in real-time.
Implementing strong access controls, such as multi-factor authentication and role-based access, can limit unauthorized access to servers and sensitive information. Regular security audits and penetration testing are essential to identify and address any weaknesses in the network security posture.
Encrypting data both at rest and in transit adds an extra layer of protection against data breaches and unauthorized access. Utilizing virtual private networks (VPNs) for secure remote access to servers can help ensure that data exchanges are encrypted and secure.
Regularly monitoring server logs and network traffic can help detect anomalous behavior and potential security incidents. Training employees on security best practices and conducting regular security awareness programs can help prevent social engineering attacks and educate users on how to safeguard sensitive information.
By adopting a multi-layered approach to network security for 2012 R2 servers, organizations can better protect their infrastructure and mitigate the risks posed by cyber threats in today's digital landscape.
Virtual Private Network effectiveness on 2012 R2 servers
Title: Enhancing Security and Privacy: The Effectiveness of Virtual Private Networks on Windows Server 2012 R2
In today's digitally interconnected world, safeguarding sensitive data and ensuring privacy are paramount concerns for businesses and individuals alike. As cyber threats continue to evolve, the use of Virtual Private Networks (VPNs) has emerged as a crucial tool for protecting data transmission over networks. When it comes to Windows Server 2012 R2, implementing a VPN solution can significantly enhance security and privacy measures.
Windows Server 2012 R2 provides a robust platform for hosting VPN services, offering built-in support for VPN protocols such as Secure Socket Tunneling Protocol (SSTP), Point-to-Point Tunneling Protocol (PPTP), and Layer 2 Tunneling Protocol (L2TP)/Internet Protocol Security (IPsec). These protocols facilitate secure communication between remote clients and the server, encrypting data traffic and ensuring its confidentiality.
One of the key advantages of utilizing a VPN on Windows Server 2012 R2 is its compatibility with a wide range of client devices and operating systems. Whether accessing the network from a Windows PC, Mac, Linux machine, or mobile device, users can securely connect to the server and access resources with ease.
Moreover, VPNs offer an additional layer of protection against unauthorized access and cyber attacks. By establishing a secure tunnel for data transmission, VPNs help prevent interception and eavesdropping by malicious actors. This is particularly crucial for organizations handling sensitive information or operating in industries with stringent compliance requirements.
Furthermore, VPNs can enhance remote access capabilities, allowing employees to securely connect to the corporate network from anywhere in the world. This flexibility not only improves productivity but also ensures that sensitive data remains protected even when accessed from outside the office environment.
In conclusion, the effectiveness of Virtual Private Networks on Windows Server 2012 R2 cannot be overstated. By leveraging the built-in VPN features of the operating system, organizations can bolster their security posture, protect sensitive data, and facilitate secure remote access for employees. As cyber threats continue to proliferate, investing in robust VPN solutions is essential for safeguarding digital assets and maintaining privacy in an increasingly interconnected world.
Server security using VPN on Windows Server 2012 R2
In the realm of cybersecurity, safeguarding server data is paramount. One effective method to enhance server security is by utilizing a Virtual Private Network (VPN) on Windows Server 2012 R2. A VPN establishes a secure connection between the server and other devices, ensuring data transmitted is encrypted and secure from potential cyber threats.
Implementing a VPN on Windows Server 2012 R2 offers numerous benefits for enhancing server security. Firstly, it encrypts the data traffic between the server and connected devices, preventing unauthorized access to sensitive information. This encryption plays a crucial role in maintaining data confidentiality and integrity, safeguarding against potential data breaches.
Moreover, a VPN provides anonymity by masking the server's actual IP address, thereby enhancing privacy and security. This makes it challenging for cybercriminals to track or intercept data transmissions, significantly reducing the risk of malicious attacks on the server.
Additionally, utilizing a VPN on Windows Server 2012 R2 allows for remote access to the server securely. Whether accessing the server from a different location or using public Wi-Fi networks, a VPN ensures that data exchanges remain protected against potential security threats.
In conclusion, incorporating a VPN on Windows Server 2012 R2 is a proactive measure to fortify server security and safeguard critical data. By encrypting data traffic, providing anonymity, and enabling secure remote access, a VPN serves as a robust defense mechanism against cyber threats, ensuring a more secure server environment.
Establishing VPN connection on 2012 R2 servers
To establish a VPN connection on Windows Server 2012 R2, follow these steps:
Begin by logging in to the server using an account with administrative privileges.
Open the "Server Manager" application from the taskbar or start menu.
In the Server Manager window, click on "Add roles and features."
Proceed through the wizard until you reach the "Server Selection" screen. Here, select the appropriate server from the server pool and click "Next."
On the "Server Roles" screen, select "Remote Access" and then click "Add Features" to install the required role services.
Click "Next" through the following screens until you reach the "Role Services" screen under the "Remote Access" role. Here, select "Direct Access and VPN (RAS)." Click "Add Features" if prompted.
Continue with the wizard to install the selected role and role services.
Once the installation is complete, open the "Routing and Remote Access" console from the Server Manager.
Right-click on the server name and select "Configure and Enable Routing and Remote Access."
Follow the configuration wizard, selecting "Custom configuration" and then "VPN access."
Complete the wizard with the default settings or configure as needed for your network environment.
Once the configuration is complete, users can establish a VPN connection to the server using a VPN client and the server's public IP address or hostname.
By following these steps, you can successfully establish a VPN connection on Windows Server 2012 R2, providing secure remote access to your server resources.
0 notes
Text
can ping host through vpn but cannot traceroute
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can ping host through vpn but cannot traceroute
Ping host through VPN
Title: How to Ping a Host Through VPN: A Step-by-Step Guide
Pinging a host through a VPN adds an extra layer of security and privacy to your network communication. Whether you're troubleshooting connectivity issues or assessing network performance, using a VPN ensures that your data remains encrypted and your identity protected. Below is a step-by-step guide on how to ping a host through a VPN:
Choose a Reliable VPN Service: Select a reputable VPN service provider that offers robust encryption protocols and a wide range of server locations. Ensure that the VPN provider has servers in the location of the host you intend to ping.
Install and Configure the VPN Client: Download and install the VPN client software on your device. Follow the setup instructions provided by your VPN service provider to configure the VPN connection properly. This typically involves entering your login credentials and selecting a server location.
Establish a VPN Connection: Launch the VPN client and establish a connection to the VPN server. Once connected, your internet traffic will be encrypted and routed through the VPN server, masking your IP address and location.
Open the Command Prompt (Windows) or Terminal (Mac/Linux): To ping a host, you'll need to access the command-line interface of your operating system. On Windows, search for "Command Prompt" in the Start menu. On Mac/Linux, open the Terminal application.
Enter the Ping Command: In the command-line interface, type the following command: ping [host IP address or domain name]. Replace [host IP address or domain name] with the IP address or domain name of the host you want to ping. Press Enter to execute the command.
Analyze the Results: After executing the ping command, you'll see the results displaying the round-trip time (RTT) and packet loss percentage. This information helps assess the network connectivity and latency to the host through the VPN connection.
By following these steps, you can effectively ping a host through a VPN, ensuring secure and private communication while troubleshooting network issues or monitoring network performance. Remember to disconnect from the VPN once you've completed your tasks to conserve bandwidth and optimize network speed.
Traceroute not working
Title: Troubleshooting Guide: Traceroute Not Working
Traceroute is a powerful diagnostic tool used to track the pathway that data takes from your computer to a destination server on the internet. However, encountering issues with traceroute not working can be frustrating, especially when you're trying to pinpoint network problems. Here are some common reasons why traceroute might not be functioning as expected, along with troubleshooting steps to resolve the issue.
Firewall Restrictions: Check if your firewall settings are blocking the traceroute packets. Firewalls, especially in corporate or networked environments, may be configured to block certain types of traffic, including ICMP packets which traceroute relies on. Temporarily disabling the firewall or adjusting its settings may allow traceroute to function properly.
Router Configuration: Sometimes, routers along the network path may not respond to traceroute requests due to misconfiguration or intentional blocking. Contact your network administrator to ensure that routers are configured to allow traceroute traffic.
Network Congestion: High network congestion or traffic may result in dropped or delayed traceroute packets, causing incomplete or inaccurate results. Try running traceroute at different times or from a different location to see if the issue persists.
Internet Service Provider (ISP) Restrictions: Some ISPs may restrict or filter traceroute traffic as part of their network management policies. Contact your ISP to inquire about any restrictions they may have and if traceroute functionality can be enabled.
Software or Hardware Issues: If traceroute consistently fails to work despite checking the above factors, there may be underlying software or hardware issues with your computer or network equipment. Ensure that your operating system and networking hardware are up-to-date, and consider seeking assistance from a professional IT technician.
By identifying and addressing the potential causes outlined above, you can effectively troubleshoot and resolve issues with traceroute not working, enabling you to diagnose network problems and ensure smooth connectivity on your network.
VPN connectivity issue
When it comes to ensuring your online privacy and security, using a Virtual Private Network (VPN) is essential. VPNs encrypt your internet connection and route it through a secure server, masking your online activities from prying eyes. However, despite the benefits of using a VPN, connectivity issues can sometimes arise, causing frustration for users.
One common VPN connectivity issue is the inability to establish a connection to the VPN server. This can be due to server downtime, network congestion, or incorrect VPN settings. To troubleshoot this issue, try connecting to different VPN servers, checking your network connection, and updating your VPN client software.
Another issue users may encounter is slow VPN speeds. This can be caused by a variety of factors, such as a distant server location, high server load, or limited bandwidth. To improve VPN speed, try connecting to a server closer to your physical location, using a less congested server, or upgrading to a VPN plan with faster speeds.
Furthermore, VPN disconnections can be a recurring issue for some users. This can happen intermittently due to network fluctuations, software conflicts, or outdated VPN protocols. To address this problem, try changing VPN protocols, updating your VPN client, or contacting your VPN provider for assistance.
In conclusion, while VPNs are crucial for maintaining online privacy and security, connectivity issues can sometimes occur. By following the troubleshooting tips mentioned above, users can resolve these problems and enjoy a seamless and secure VPN experience.
Network troubleshooting VPN
In the world of digital networking, Virtual Private Networks (VPNs) play a crucial role in ensuring secure connections and safeguarding sensitive data. However, like any technology, VPNs can occasionally run into issues that require troubleshooting to resolve.
One common issue that users may encounter when using a VPN is difficulty in connecting to the network. This can be caused by various factors such as server maintenance, network congestion, or incorrect settings on the user's end. To troubleshoot this problem, users can try switching to a different server location, restarting their device, or checking their VPN configuration settings.
Another common problem with VPNs is slow connection speeds. Slow speeds can be frustrating and may be due to factors such as server overload, distance from the server, or limitations imposed by the user's internet service provider. To address this issue, users can try connecting to a different server, optimizing their internet connection, or upgrading to a higher-tier VPN subscription with faster speeds.
DNS leaks are another issue that can compromise the privacy and security of a VPN connection. A DNS leak occurs when the device sends DNS queries outside of the encrypted VPN tunnel, potentially exposing sensitive information. Users can prevent DNS leaks by configuring their VPN client correctly and conducting regular leak tests using online tools.
By familiarizing themselves with these common VPN troubleshooting issues and solutions, users can ensure a seamless and secure online experience while harnessing the full potential of Virtual Private Networks. Whether it's connectivity issues, slow speeds, or DNS leaks, understanding how to troubleshoot VPN problems is essential for maintaining a reliable and secure network connection.
Cannot trace route through VPN
When you are unable to trace a route through a Virtual Private Network (VPN), it can be quite frustrating and can signify potential issues with your network settings or VPN configuration. Tracing a route through a VPN is a common troubleshooting technique used to identify any connectivity issues and determine the path that network packets take from your device through the VPN server.
If you find yourself unable to trace a route through your VPN, there are several possible reasons for this. One common reason could be misconfiguration in the VPN settings on your device or the VPN server itself. Double-checking the settings and ensuring that they are correct is crucial in such situations.
Another reason could be firewall restrictions blocking the traceroute packets from passing through the VPN connection. Adjusting the firewall settings to allow the traceroute packets can help you troubleshoot the issue.
In some cases, the VPN server might be configured to block traceroute requests for security reasons. Contacting your VPN service provider to inquire about their traceroute policies and potential solutions could help resolve the problem.
Ultimately, if you cannot trace a route through your VPN, it is recommended to review your VPN settings, check for any firewall restrictions, and reach out to your VPN provider for assistance if needed. Proper configuration and troubleshooting can often resolve such issues and ensure smooth connectivity through your VPN.
0 notes
Text
What is IPSec and how does it work?
What is an IPSec article and how does it work? Get acquainted (gain, obtain) with present-day techniques that came from IPsec Protocols, which are used to set up encrypted connections between two or more devices. These types of protocols help keep data sent over public networks secure. You should know that IPsec is often used to set up V.P.N. VPN, which is done by encrypting IP packets and authenticating the packet source.
What is ip?
IP stands for Internet Protocol, which is the main routing protocol used in the Internet. This protocol specifies where the data should travel and which destination it should reach. But the IPSec protocol also adds encryption and authentication to the process.
Who made IpSec?
This protocol is a joint product of Microsoft and Cisco Cisco Systems works by authenticating and encrypting each data packet in a data stream.
What port does IPsec use?
The software port or network port is where the information is sent. In other words, a port is a place through which data enters or leaves a computer or server, and a number is assigned to each of these ports, which are between 0 and 65535. IPsec also typically uses port 500 to perform encryption and decryption algorithms.
What are the benefits of IPSec?
Replay attack protection: Assigns a unique number to each data packet (packet) which deletes the packet if that number is duplicate.
Confidentiality of information or encryption: VPN connection security is increased by PFS in this protocol, which is done by creating a unique key in each connection.
Information source authentication: Confirmed by the message authentication code (HMAC)
That message has not changed.
Transparency: Ipsec works at the network layer, which is actually transparent to applications and users. As a result, there is no need to change the routers and firewalls during use
Dynamic re-encryption: The security keys for decryption change at regular intervals. This prevents identity theft and hacker attacks.
Replay attack protection Any software can be compatible with this protocol Confidentiality of information (encryption) Having transport mode Having tunnel mode Authentication of the source and origin of information Layer 3 or Network Authentication.
Types of IPSec IPSec security protocols
IPsec is an open source standard and part of the IPv4 suite. IPsec can communicate between both transport mode and tunnel mode. IPsec is a global standard and can perform a variety of security processes using a set of protocols it uses, including the protocols used in IPsec. To give privacy to the data and finally Security Associations or SA to create the data used in AH and ESP.
1. IPSec AH protocol The Authentication Header (AH) protocol was developed in the early 1990s in the United States Naval Research Laboratory. This protocol ensures the security of the data source by authenticating IP packets. In this algorithm, using the sliding window method and deleting old packets and assigning a sequence number, the contents of the IPsec packet are protected against attacks such as replay attacks. In fact, with this technique, one can only be sure that the data packets have been sent from a reputable source and have not been tampered with.
In this case, both the upload and the header are encrypted. The term Tunnel is used instead of AH. All data is protected by HMAC. And only peer-to-peer points know the secret key made by HMAC and can decrypt it. And as mentioned, because headers are also encrypted and can not be changed in networks where NAT is done, the VPN service can not be used.
Integrity of submitted data Data source authentication Reject resended packages 2. IP Encapsulating Security Payload (ESP) The IP Encapsulating Security Payload (ESP) protocol was developed at the Naval Research Laboratory in 1992 as part of a DARPA-sponsored research project. The work of this protocol ensures data authentication through the source authentication algorithm, data integrity through the hash function, and confidentiality through IP packet encryption. ESP is used in settings and configurations that support either encryption only or authentication only. This is a weakness because it is unsafe to use encryption without authentication.
In this case, only the upload is encrypted and the headers remain the same without change. The term Transport is used instead of ESP. In this method, both parties must perform authentication operations and also the data is sent in encrypted form.
In fact, unlike the AH protocol, the ESP protocol in Transport mode does not provide integration and authentication for the entire IP packet. In Tunnel mode, where the entire original IP packet is located with a new packet header, ESP protects the entire internal IP packet (including the internal header) while the external header (including external IPv4 options or IPv6 extension) remains unprotected. They stay.
3. Security association IPsec protocols use a Security Association to create interconnected security features such as algorithms and keys. In fact, when the AH or ESP protocol is specified to be used, the Security Association provides a wide range of options. Before exchanging data, the two hosts agree on which algorithm to use to encrypt the IP packet. The hash function is used to ensure data integrity. These parameters are agreed in each session that has a specific life (time) and also a specific key must be specified for each session.
In how many modes can IPSec work? (Operation Modes)
IPsec AH and IPSec ESP protocols can be used in host-to-host transport mode as well as in network tunneling mode.
1. IPSec Transport Mode In transport mode, only the encrypted or verified IP packet and routing remain intact because the IP header is neither modified nor encrypted. However, when the authentication header is used, the hash value is invalidated and the IP addresses cannot be modified and translated with the Network address translation method. The Transport and Application layers are always secured with a hash, so they can not be modified in any way, even by translating port numbers.
2. Tunnel Mode or IPSec Tunnel Configuration In Tunnel mode, the entire IP packet is encrypted and authenticated. It is then categorized in a new IP packet with a new IP header. From tunnel mode to create virtual private networks for network-to-network communication (e.g. between routers to link sites), host-to-network communication (e.g. remote user access), and host-to-host communication (e.g. Private chat) is used.
Key management in IPSec protocol
IPSec is widely used in VPN technology for authentication, privacy, integrity and key management in IP-based networks.
IPSec establishes communication security within network equipment with the help of secure encryption services. For IPSec to function properly, both the sender and receiver must share a public key, which is achieved through the use of the "key management" protocol. This protocol allows the receiver to obtain a public key and authenticate the sender based on a digital signature.
2 notes
·
View notes
Text
Protect Your Browsing/Data Sharing
For free, because in this house I don’t believe in making people pay for basic human rights.
I’ve decided to share my browsing protecting tips here. Digital security is usually quite expensive, but it doesn’t have to be! In this day and age, you’ll be told to watch out for home-born hackers and ‘hacktivists’ accessing your data, but I gotta tell you, what your own governments and ISPs are doing makes this more important (aka: they’re worse).
I know with all the TIKTOK IS SPYING ON YOU stuff, a lot of my friends have come to me seeking some advice on this. This is also great if you don’t want parents checking your browsing >_> just sayin’
If anyone has questions - drop me an ask! I’ll always answer for this topic. I am also happy to ‘expand’ on one of these suggestions if they’re unclear :)
Note: This works under the assumption you have your default ISP provided router and can’t get another one for whatever reason. I will advise that if you can get an additional router, do so! Try to avoid the one the ISP has provided to you.
Additional Note: This is not ‘optimal’. There is no such thing in security – everything has a backdoor.
Let’s get cracking! This is a long, and thorough post, but I _do _have a pdf somewhere if you want it because it looks nicer :*)
Use Tor to browse.
There you go, there’s my advice leaves
https://support.torproject.org/ to Download/Install/Run.
Don’t change anything, except maybe using Tor in ‘bridge’ mode.
Okay, you can use other browsers (see: Chrome/Firefox), but they are not as secure as Tor.
USE A VPN IF YOU ARE GOING TO USE TOR! I prefer Firefox (extensions + good security)
________________________________________________________________
Install the following extensions if you have Chrome or Firefox:
Privacy Possum
Stops tracking cookies. PSA: Cookies are not evil, certain cookies can be.
Firefox: https://addons.mozilla.org/nl/firefox/addon/privacy-possum/
Chrome: https://chrome.google.com/webstore/detail/privacy-possum/ommfjecdpepadiafbnidoiggfpbnkfbj
Ghostery
Stops tracking adverts and cookies. Why do I need this in addition to Privacy Possum? Ghostery specifically looks at tracking cookie ads. It’s like adding MOAR POWAH to Privacy Possum.
Firefox: https://addons.mozilla.org/nl/firefox/addon/ghostery/
Chrome: https://chrome.google.com/webstore/detail/ghostery-%E2%80%93-privacy-ad-blo/mlomiejdfkolichcflejclcbmpeaniij?hl=nl
HTTPS Everywhere
Enforces HTTPS. If you look next to the URL in your browser, you’ll see the little lock which indicates the specific URL is secure and uses HTTPS. Many websites still use the old HTTP, which is not as secure and you should NEVER EVER VISIT AN HTTP SITE ITS LIKE READING A BOOK OVER SOMEONE’S SHOULDER, thank you.
Firefox: https://addons.mozilla.org/nl/firefox/addon/https-everywhere/
Chrome: https://chrome.google.com/webstore/detail/https-everywhere/gcbommkclmclpchllfjekcdonpmejbdp?hl=nl
Adblock Plus
Foff, ads.* Firefox: https://addons.mozilla.org/nl/firefox/addon/adblock-plus/
Chrome: https://chrome.google.com/webstore/detail/adblock-plus-free-ad-bloc/cfhdojbkjhnklbpkdaibdccddilifddb
________________________________________________________________
DNS Settings
Ideally, you should change this on your router. ISPs use a default DNS – you don’t want to use anything those bastards say you should use.
Use Cloudflare or OpenDNS:
Cloudflare is more secure overall and keeps up to standards in addition to not storing your data, whereas OpenDNS is great at avoiding malicious websites, just take your pick really 😊There are a ton of other options, feel free to google ‘free DNS servers’. Google has it’s own as well, but, yaknow, it’s Google.
Cloudflare
Primary Server: 1.1.1.1
Secondary Server: 1.0.0.1
OpenDNS
Primary Server: 208.67.222.222
Secondary Server: 208.67.220.220
Add these to your router settings:
In a browser, go to http://192.168.1.1/ or http://192.168.1.0/ (it varies per router). This will lead to your router’s configuration portal. Don’t have a router with a configuration portal? Throw it in the trash and tell your ISP they suck for giving it to you.
Login to the admin portal. If you have not configured this or set a password, try the default combinations: usernames are usually ‘admin’ or blank, the passwords are usually blank, ‘admin’, or ‘1234’.
Each router is different, navigate to where it asks for DNS values or servers, and enter the above addresses. You will see ‘Static’ near the DNS options, select it. This also ensures you’re in the right place. If you’re not sure what to do, look up the model/make of your router and check how you can change DNS.
Whilst you’re at it, change your WiFi password from the default one, and create a proper password for the WiFi portal login. If these two things are kept as default, all these protection methods are pointless as it is easy to crack your router passwords.
Can’t do this on your router because your parents are ds?* No worries! This can be done on your device! :) Yeah, I know how parents work.
Windows OS
Go to Control Panel <Network and Internet < Network and Sharing Center
Click on the link next to “Connections:”* Click “Properties” in the dialogue that pops up.
Select Internet Protocol Version 4 < Click Properties < Select “Use Following DNS Servers” < Enter the primary and secondary server addresses
Do this again for Internet Protocol Version 6 in the list.
Boom. Windows is so nice to make this easy.
Mac OS
Go to Apple Menu < System Preferences < Network
Select the Network you’re connected to
Click Advanced
Select DNS Tab
Click the + button < Enter chosen DNS < Save
Linux OS
I’m going to assume if you’re using Linux, you know how to use the terminal and are using a modern Linux system. Enter these line by line. There are many ways to do this (Google is your friend)
· sudo apt update
· sudo apt install resolvconf
· sudo systemctl status resolvconf.service (check that it is running)
· sudo systemctl start resolvconf.service (to start it, use ‘enable’ instead of ‘start’ to enable)
· sudo nano /etc/resolvconf/resolv.conf.d/head
· nameserver YOUR.DNS.ADDRESS.HERE
· nameserver YOUR.SECOND.DNS.ADDRESS.HERE
· sudo systemctl start resolvconf.service
Android
Oh yeah, you can do this on phones too wiggles eyebrows. Note, if you’re using a VPN it will lock you out of editing this. Turn it off, edit your DNS, turn it back on. This can be tricky with mobile devices that have not been jailbroken (I don’t advise doing that if you have no clue what you’re doing).
Go to Settings < Connections < WiFi
Select the gear icon next to your current WiFi
Select Advanced < Ip Settings drop-down < Static
Enter chosen DNS options under “DNS 1” and “DNS 2”
iPhone
Go to Settings < Wi-Fi
Select the arrow button next to your current WiFi
Select DHCP tab, scroll down to DNS
Select DNS, and enter your DNS servers
TEST YOUR DNS IS WORKING:
OpenDNS: https://welcome.opendns.com/ (You’ll see a “Welcome to OpenDNS” message”
Cloudflare: https://www.cloudflare.com/ssl/encrypted-sni/ (You’ll see check marks for all fields)
________________________________________________________________
Turn of WPS on router. Enable encryption on router.
If you can access your router portal, find any sort of toggle or field that says “WPS” and disable it. WPS= bad.
Wherever there is an option for WPA2 (or higher) to enable, enable it.
Enable the firewall on your router and Operating System – ALWAYS. If you disable this, you’re disabling an additional layer of security. Firewalls are confusing things and a royal pain in the ass to configure, but having the default is better than having nothing.
________________________________________________________________
Configure your browsers.
Browsers have most things enabled by default, including tracking your location, turning your microphone on etc. Let’s disable that nonsense and make them ask you for permission because it’s 2020.
I’m using Chrome as an example below because it is INFAMOUS for this. Essentially, go through your browser and scroll through settings you don’t like.
Go to the little menu icon < select “Settings”
Sign out if it’s linked to your Google account. Let’s not give Chrome a reason to track your browsing history for your account >_>* Disable EVERYTHING:
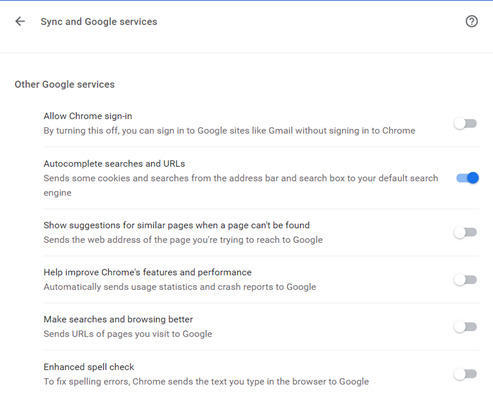
Here, I turned off everything I would find annoying except autocomplete because I’m lazy.

NICE TRY GOOGLE, YOU CANT SAVE MY CREDIT CARD. (Seriously, don’t ever EVER autosave passwords/payment info).

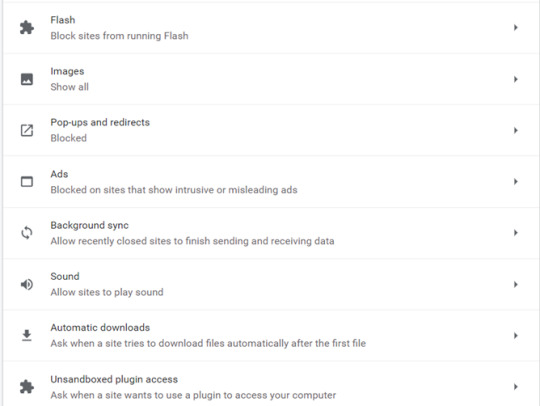
The trick is to balance ease of use with security. These may vary from person to person, in general though, if there’s a setting ‘ask before etc.’ select that over ‘allow’.
As a rule of thumb:
NEVER ENABLE FLASH (not even an ‘ask before’), NEVER ENABLE LOCATION (ask before is fine, but at your own risk), NEVER ENABLE CAMERA (ask before is fine, but at your own risk, use the desktop version of an application over the browser version), NEVER ENABLE MICROPHONE (same as camera)
________________________________________________________________
Additional Tipss
Check every single social media setting. You should disable anything that accesses your privacy, if possible.
Cover your camera with a sticker. Disable it unless it’s needed
Disable your mic unless you need it.
Turn off Bluetooth/NFC when you don’t need it.
Have two separate networks/Wi-Fi for smart devices and personal devices.
Always use two/multi-factor-authentication for every single app, site, device etc. that you can.
Biometrics are preferable and the usual chosen default (fingerprints, retina scan, NOT FACE OR VOICE THIS IS SO EASY TO IMMITATE BRO PICTURES ARE A THING)
SMS (try to avoid if you can, please)
App ‘token’ authentication. A good choice if done well.
Hard physical key or token. The best option (Google: Yubikey, for some information on how this works).
Passwords
I know you use the same password for everything – get a centralized password manager, and start using different ones. Examples include PasswordSafe, Keeper, Bitdefender etc. Try go for a Cloud provider, and pay a little bit for the extra security and backup. If they’re compromised, then you will know, and you’ll be able to change everything. You can tie password managers to a token too.
USE PASSPHRASES, 17 characters is a good average length, use a mix of characters, uppercase, lowercase, numbers, ascii etc.
It doesn’t matter if your password is ‘complex’, it matters if it is complex and long. Servers and computers these days are jacked up on tech steroids and can bruteforce many things, given enough time.
Anti-virus.
EVERYONE SHOULD HAVE ONE, ON EVERY DEVICE. If you have a device that can add AV, add it. This goes for phones, PCs, smartTVs, you name it.
Free versions are okay, some free ones I like are Bitdefender, Kaspersky, McAfee, Avast (hate their fihsfirstg89ewjg9srjgrd ads though).
Sorry Mac users, that belief that you don’t need one is from 2008. Windows has more security built in than Mac, which means Mac devices should 100% make sure they are adding an AV.
VPN
Ahhhhh. The great VPN. A tricky one. Most free versions I find incredibly slow, but give them a try – play around! A VPN is an excellent addition and these days, I’d argue it’s an absolute must. Many AV solutions include a VPN package with their deal. If you want to make sure those sites don’t share your data, this is the thing that will hurt the most - a good VPN will make it a jumbled mess.
Updates - just do them.
There is no complete security in this day and age – it really is just a matter of time. If you use social media, you’re traceable, be it by the company, ISP, some bored 10 year old, or your ex, your data is out there circulating. Once it’s on the internet, it’s there forever, so don’t worry too much and try to make sure it’s all complex binary trash so that they open it and go “WTF” 😊
#tiktok#security#it security#data#data privacy#private browsing#facebook#google#data theft#third party ad#ads#secure browsing#protect data
12 notes
·
View notes
Text
How to fix io.netty.channel Minecraft Error

There are a lot of people who are not able to connect to Minecraft server. According to reports they fail to connect to the server because of certain error with time out error. But there are certain ways in which you can easily fix the io.netty.channel.minecraft error. The consistent error process is observed for both single player as well as multiplayer servers. Reason behind the Minecraft server refusing the error is the common connectivity issue. Apart from that a couple of reasons are sorted out for that, these can be backdated JAVA software or blocking of the server by the windows firewall else an unstable software.
Moving ahead with how to fix it ;
First the users can add exceptions to the firewall settings in the Minecraft folder and it’s probably the best option. The reason can be, VPN and windows firewall are responsible for blocking the access to Minecraft server. There are even some exceptions in the firewall to avoid abstract channel, that is annotated connectexpection connection refused error.
The users can check out and delete the unstable software which creates conflict after installing to the computer. For this, the users can check the list of software that is not compatible with the Minecraft game.
Add on the IP address and then select suitable working port. With the working process the users need to run the command prompt as administrator and then browse to the Minecraft servers.
Next reset the modem or router which is the most straight forward solution. If the internet or modem is considered as the cause of the problems then you can easily notice the Minecraft error. So it’s important that you check out the internet connection before trying to connect to the server.
You can try with switching off the router for some time and then get power back on with restart of the router.
Try to next connect to the server after resetting the router.
Read More..
#cybersecurity#fix io.netty.channel.connectiontimedout#fix io.netty.channel minecraft error#how to fix minecraft error#minecraft java error#minecraft server error io.netty.channel#minecraft connection timed out
2 notes
·
View notes
Text
Webdav Server Windows 10

Windows 10 Connect To Webdav
Webdav Server Windows 10 Einrichten
WebDAV on Windows 10 How to access MyFiles off-campus using WebDAV on a Windows 10 PC From the Start Menu go to File Explorer and select This PC on the left hand pane. How to create a WebDAV server on Windows and connect it to ONLYOFFICE Community Server v.10.0 Community Server changelog. Open in new window. Version 10.0.4. Release date:. General portal changes. The Mono version used is updated to 6.0. To create a WebDAV server.
WebDAV is an FTP-like protocol you can use to remotely access or share your files over the Internet. In contrast to FTP, though, WebDAV works better through firewalls and can be password-protected and encrypted. In our latest server tutorial we'll share how to set up the WebDAV server that's included with Windows.
First, you must install the Internet Information Services (IIS) and WebDAV publishing features of Windows. In Windows 7, click Start, type 'Windows features,' and then click enter. In Windows 8, go to the Start screen, type 'Windows features,' select 'Settings' on the right, and then select the shortcut that appears.
Make sure you select at least the following:
Internet Information Services
IIS Management Console
WebDAV Publishing
Windows Authentication

Next, to enable the WebDAV publishing you must open the IIS Manager. In Windows 7, click Start, type 'IIS,' and open the shortcut that appears. In Windows 8, go to the Start screen, type 'IIS,' and then select the shortcut that appears.
To configure the authentication, select the 'Default Web Site' and double-click the 'Authentication' icon. The list of authentication types displayed will depend upon which ones you installed earlier, but I'd suggest disabling 'Anonymous' and enabling 'Windows Authentication' if you will only be using IIS for WebDAV.
Next, select the 'Default Web Site' site again and double-click the 'WebDAV Authoring Rules' and then click 'Enable' on the right. Now click 'Add Authoring Rule' on the right to configure the permissions and make your desired selections.
To test if IIS and the web server are running, open a web browser and type 'localhost' and hit Enter.
If you enabled Windows Authentication, you'll be prompted for a username and password, so enter your Windows account name and password here. If you have issues signing in, make sure you're using the correct account name — open the Computer Management console to check the local users list to confirm.
Once you've authenticated, you should next see the default webpage of IIS if you haven't already deleted or replaced it.
To test the WebDAV server in action, open a command prompt and type: net use * http://localhost. This should map a network drive to your WebDAV folder, showing just the files from your IIS web server directory.
If you want to offer access to other places you can add some virtual directories by right-clicking the Default Web Site and choosing 'Add New Virtual Directory.'
In order for you or others to access the WebDAV server share via the Internet, you must configure your firewall to open port 80 for unencrypted access and/or 443 for encrypted access, as well as configure your router to forward these ports to the Windows PC. Once properly configured, to access the WebDAV share via the Internet you'd use either your Internet IP address or a domain or host name if you have one configured.
While your WebDAV password is encrypted when using Windows Authentication, the rest of your session is sent in the clear if you choose to use normal HTTP via port 80. But you can also encrypt the entire session by enabling SSL encryption in IIS and using the HTTPS address when configuring/accessing the WebDAV share.
If you'd like to be able to see a listing of your files in a web browser, turn on Directory Browsing in IIS. Select the Default Web Site, double-click 'Directory Browsing,' and then click 'Enable' on the right.
Windows 10 Connect To Webdav
Eric Geier is a freelance tech writer — keep up with his writings on Facebook. He's also the founder of NoWiresSecurity, a cloud-based Wi-Fi security service, and On Spot Techs, an on-site computer services company.
Webdav Server Windows 10 Einrichten
Follow ServerWatch on Twitterandon Facebook

1 note
·
View note
Text
Top 7 Fastest VPNs of 2020
What a VPN is... And what it isn’t
First of all, you still need to preserve your everyday ISP. Using a VPN will no longer update your ISP’s dollars-per-month invoice, but an amazing VPN will act as a cloaking device. All your ISP will see is you having access to anything your VPN makes a decision to show while you connect with your preferred Internet vacation spot.
Second, maximum reputable VPNs will price a subscription price for a motive. You use their offerings, frequently called a tunnel to the Internet. They now personal your information, so you’re paying them to shield your privacy.
Next, your VPN basically turns into your encrypted proxy. Wherever your VPN is, that is additionally where the Internet considers you to be. All roads monitoring your Internet activity will lead returned on your VPN. Do check: ipvanish black friday
Finally, due to the fact a VPN uses encryption, you can file-share and down load securely to coronary heart’s content—even from public WiFi hotspots—as long as your VPN helps peer-to-peer (P2P) record-sharing.
The alternate-off to all of this, of course, is that every one that encryption and additional layers of security can slow Internet get admission to. That’s why it pays to realize precisely which VPNs are maximum probably to maintain you now not best safe and relaxed however additionally up to speed. Here are our top picks, some want-to-recognise specifications and some nods to what makes them special.
Choosing a VPN Political, societal and technological shifts handiest increase the significance of security, anonymity, statistics usage, P2P report-sharing and torrenting competencies, and bandwidth and velocity. Subscription charges vary from the loose—and regularly slow, insecure and volatile—to the high-priced. However, nice VPN providers have a tendency to vary with the aid of just a few greenbacks. When looking for your plan, make certain to recall the following:
Security—as a minimum 256-bit encryption. Compatibility with hardware and software. Server and IP cope with availability and place. Country of registration and information retention laws. Bandwidth or information restrictions, consisting of throttling. Servers unique for P2P report-sharing, torrenting or different designations. Firewalls. Proxies like SOCKS5. Kill switches. Split tunneling and talents for manual configurations. Customer service and help. Considering speed with VPNs When it comes to hurry, understand that a VPN in reality puts a unique license plate in your carload of records inside the flow of visitors. The pleasant VPNs won’t sluggish you down by using a good deal. However, you could occasionally have to weigh protection against speed, and any VPN still relies at the underlying download and upload speeds that your ISP permits.
1. ExpressVPN ExpressVPN is a first rate first pick in a test of VPN speed because we can begin with its VPN Speed Test. This handy menu device types the servers and assigns every a pace index based totally on essential factors:
Latency — the milliseconds’ information travels among your device and a VPN server Download speed — how many kilobits in line with second or Kbps. Based inside the British Virgin Islands, Express substances extra than 1,000 servers in a hundred forty five VPN server places in ninety four nations. Just run your speed check and megastar your favorites.
This VPN is known for its stability of HD streaming abilties, P2P record-sharing, and security features. It supports all gadgets, from mobiles and computers to routers, and any connection— stressed out Wi-Fi or cellular. It allows three simultaneous connections, making it the most limited of our pinnacle selections (however, one of those may be a router). As for its other features, you could anticipate:
Compatibility with Windows, Mac, iOS, Android, Linux, and routers. Protocols OpenVPN TCP/UDP, SSTP, L2TP/IPsec and PPTP. AES-256-bit encryption ingoing and outgoing.
Unlimited bandwidth, velocity, and server switches. DNS Leak Test device and Express help to remove any leaks. Network Lock, ExpressVPN’s kill transfer for Windows and Mac. Shared IP addresses.
Split tunneling and inverse split tunneling to shield precise connections. Supports VoIP. P2P and torrent-friendly.
Zero logging, with site visitors blending. Terms of provider kingdom that they do music connection dates, server and amount of information strictly for analytics. A full menu of payment alternatives such as credit card, Bitcoin, PayPal and more. Intuitive internet site with lots of informative screenshots and help. Round-the-clock customer service through live chat or e mail.
2. NordVPN Like the alternative six on our list, Nord uses AES-256-bit encryption for all traffic, both incoming and outgoing. However, this VPN adds a second layer to act as a double VPN, encrypting data flowing between your device and your first DNS server and alternatively at a second server before the visitors meets the Internet. Incoming definitely reverses the manner.
Just 5 years antique and based totally in Panama, NordVPN has approximately 1,000 servers in fifty nine nations. It is one of the maximum generous of our selections, allowing an impressive six simultaneous connections. However, each must use a extraordinary protocol. You have 4 options—OpenVPN TCP/UDP, L2TP and PPTP—so essentially, in case you want to apply all six devices straight away, you’ll ought to break up between two or greater servers. Nord does guide routers—which count as one—as well as all other mobile and desktop gadgets. As for the capabilities rundown, NordVPN gives:
Compatibility with Windows, Mac, Android and iOS, with custom software program available. Protocols OpenVPN TCP/UDP, L2TP and PPTP; confined IKEv2/IPsec. IPv6 support expected for 2017. AES-256-bit double-layer encryption ingoing and outgoing. Unlimited bandwidth and velocity. Automatic kill switch for Windows, Mac and iOS. Identified double VPN, Onion over VPN, anti-DDoS, devoted IP, general VPN and P2P servers. Ultra Fast TV and P2P-optimized servers; permits torrenting. Supports VoIP. Supports SOCKS5 and HTTPS proxy servers. Smart Play relaxed proxies to circumvent geoblocking and permit content streaming.
Option for upload-on committed IP server and static IP deal with in U.S., U.K., Germany or Netherlands. Zero logging. Full menu of price options consisting of credit cards, Bitcoin, PayPal and extra on Paymentwall. Well-maintained internet site with useful FAQs page and dietary supplements. 24/7 customer support thru stay chat, email, Nord’s price ticket gadget, Facebook or Twitter.
Three. IPVanish IPVanish is based in Florida’s Orange County. IPVanish is thought for its speed and being torrenting- and P2P-friendly—making it a fave for game enthusiasts. The organization boasts greater than 750 servers in at the least 60 countries, with more than forty,000 IPs general and as a minimum 10 specific—often more—shareable IP addresses per server.
IPVanish permits five simultaneous connections on a couple of gadgets—such as routers—at the four protocols—OpenVPN TCP/UDP, L2TP and PPTP—in addition to IPSec and IKEv2 for iOS. IPVanish consists of SOCKS5 in all its plans, which means that which you have the option of passing traffic—downloading torrents, for instance—thru an nameless high-pace, offshore proxy. In addition, the carrier consists of:
Compatibility with Windows, Mac, iOS, Android, Linux Ubuntu and Chromebook. Protocols OpenVPN TCP/UDP, L2TP and PPTP; IPSec and IKEv2 for iOS and IPv4. AES-256-bit encryption ingoing and outgoing. Unlimited bandwidth and server switching. SOCKS5 proxy. IP address biking. Support of VoIP. Unlimited P2P supporting BitTorrent. NAT firewall. Kill transfer for Mac OS X and Windows. No traffic logs.
Extensive charge options including credit score card, Bitcoin, PayPal and plenty of others. Extensive website. Technical records, but, can be hard to discover. Support to be had thru electronic mail. When we checked, there was a wait of about 36 hours.
Four. PureVPN
Celebrating “10 years of safety,” PureVPN claims greater than 1,000,000 users and guarantees them “entire freedom” and “global-class” safety on both a personal and enterprise scale. The company is primarily based in Hong Kong, which has no mandatory facts retention laws—why many individuals pick a VPN inside the first area.
Meanwhile, PureVPN is a connectivity maven. Its community covers 141 nations with 180 places and more than 750 servers. It allows five simultaneous connections for greater than 20 exclusive devices. Its virtual router feature allows you to show any Windows pc or computer into a digital router for up to ten gadgets. On pinnacle of that, PureVPN writes its personal code for all of the primary structures and uses no third events for real statistics transfer. PureVPN covers all of the fundamental desirables like:
Compatibility with Windows, Mac, iOS, Android and Linux. Selection of protocols—OpenVPN TCP/UDP, PPTP, L2TP, IKEv2/IPsec and Stealth. IPv6 leak safety for Windows and Mac. AES-256-bit encryption ingoing and outgoing. Unlimited bandwidth, facts transfer and server switching. Split tunneling for Windows and Android. File-sharing restricted to specified servers. Kill switch for Windows and Mac.
Optional add-on dedicated IP and static IP address. Zero logs. Extensive fee alternatives—credit score playing cards, PayPal, Alipay, assorted Bitcoin organizations, Paymentwall and Cashu. Very consumer-friendly, intuitive website with seek option. 24/7 stay chat pop-up for assist.
Five. VPNArea Based in Bulgaria, VPNArea opened store in 2012, with its headquarters servers and electronic mail hosted in Switzerland. The organization is committed to keeping a speedy consumer-to-server ratio, citing a server for every 250 clients. It’s now up to more than two hundred servers in 68 international locations and greater than 10,000 IP addresses.
Another generous VPN issuer, VPNArea permits you six simultaneous connections to your favourite devices, together with routers, through OpenVPN TCP/UDP, PPTP or L2TP. It also gives its very own Chameleon app for Windows. Like a number of different vendors—however no longer all—VPNArea’s service consists of a kill switch machine; in case your VPN service drops for a few cause, your IP deal with will stay covered. VPNArea’s carrier also affords:
Compatibility with Windows, Mac, Android, iOS and Linux. Protocols OpenVPN TCP/UDP, PPTP or L2TP. IPv6 and WebRTC leak protection. Chameleon OpenVPN software program for Windows. AES-256-bit encryption ingoing and outgoing.
Unlimited bandwidth and server switching. Shared IPs, with adjustable car random IP changer. Speed check with ping and download in addition to users on-line server load screen. Kill switch device.
P2P permitted on distinct servers. Account sharing. Custom business accounts available. Optional add-on personal VPN server with dedicated IP cope with $15 a year. No logs. Payment options restricted to Visa, MasterCard, PayPal, Payza and Bitcoin. 24/7 help to be had through stay chat, electronic mail and Skype.
6. Buffered Buffered VPN is the youngster in our seven. Registered in Budapest, Hungary, in 2013, it has servers in 37 international locations and guarantees that in case you don’t see the only which you need, they just might be capable of get one for you. This VPN is enthusiastic about preserving freedom of speech and access to data irrespective of in which you're. Buffered no longer most effective says that it’s torrent-pleasant however is also cited for being so.
Buffered allows customers five simultaneous connections and houses in on the want for comfortable velocity with out the constraints of throttling. It gives some of the offerings you would anticipate with a few obstacles:
Compatibility with Windows, Mac, Linux, iOS, Android in addition to DD-WRT and Tomato routers. Exclusively OpenVPN TCP/UDP protocols. Supports IPv4. 256-bit Blowfish encryption. Friendly to P2P record-sharing, torrenting, gaming and streaming. Unlimited bandwidth, speed and server switching Optional add-on dedicated server with static IP cope with. Supports VoIP and Skype. NAT Firewall.
Dynamic IP addresses. Will set up servers upon request. Does no longer allow split tunneling. No kill switch. No logs policy. Salesy website. All the technical records—everything you really want to realize—is within the internet site’s FAQs phase and tutorials. Payment menu includes the primary credit playing cards, Maestro, JCB and PayPal. 24/7 guide via stay chat with Knowledge Center.
7. VyprVPN VyprVPN is sincerely a Golden Frog introduction included in Switzerland, which—because the Golden Frog site explains—has set up safe harbors with the EU, the U.S. And other countries. These folks take their security critically. Their very own inhouse engineers write their code. They very own and manage all their own hardware and software and keep their operation inhouse, and not using a 1/3 parties. They’ve were given more than 700 servers and 2 hundred,000 IP addresses spanning the globe, supplying cease-to-stop privateness.
If you need a seasoned bono download of a GB to strive out the VPN, you may sign on for VyperVPN Free. Just choose your app at the website—it really works for desktops in addition to iOS and Android. You could have two simultaneous connections and get right of entry to to the Cypher encrypted messaging app. It’s a one-time deal, but you could without problems improve to a subscription.
A lot of misunderstanding exists over the feature of split tunneling, and Vypr isn't any exception. At its only, the exercise lets in customers to consist of or exclude certain devices or applications, putting a few below VPN protection while permitting others to interface or stream at once out of your ISP. Not all VPNs even provide it. The configuration that VyprVPN uses allows split tunneling with the aid of app. In addition, a subscription comes with:
Compatibility with Windows, Mac, iOS, Android, Linux, TVs, OpenELEC clever gadgets, routers and extra. Protocols OpenVPN TCP/UDP, L2TP/IPsec, PPTP and Chameleon. 256-bit encryption. Unlimited bandwidth, pace and server switching. Golden Frog-optimized code for cutting-edge broadband connections. NAT Firewall. SOCKS5 proxy supported.
Dynamic server switching. Kill switch in Windows and Mac. Split tunneling for apps however now not servers or gadgets. Desktop and mobile apps, consisting of Blackphone and Anonabox. Chameleon proprietary metadata scrambler for Windows, Mac, Android and routers.
Conclusion: Zero-know-how VyperDNS provider preserves privateness and geolocational get right of entry to, defeats censorship and geoblocking. User-pleasant, exceptionally informative website with the entirety inside the right place—just in which you’d placed it. No logs. End-to-end code, possession and management.
1 note
·
View note
Text
Hacked (Tim)
You get home and begin to work on decoding the signal that is tagging off of Wayne Industries. It's not new. Just subtle and has access to EVERYTHING. Maybe Mr. Wayne would hire you if you cut it off, or maybe it is from Batman. If it is Batman could easily get in and send them some help. Maybe learn who they are and see if they can crack your personal coding fire walls.
You easily separate the signal that piggybacks the Wayne Industries security and find it is labels "Bat-security" making it quite obvious who it belonged to. Really original Batman...
After about an hour, and two cups of coffee, at keying away you get the password, Batword, to the feed which causes security camera feeds from all across Gotham to pop up on the edges of the screen and a window in the center with the bat symbol and a password box in the center. After trying the Batword password on this screen you pull up a new command prompt and tap away at the keyboard.
Another hour later, and another cup of coffee, you manage to not only get into the base files on the main system but open a chat box to a computer that is online. The files that you open, one by one tell you who is who (secret identities, past details, birthdays, allergies, and so forth). Before sending a message you turn on your personal firewall, glance at the video feed from the computer that you can watch all parts of, and get a devious plan.
How infuriating would it be to spend hours decoding a password, that will only allow him to message me back, and have it be his name.
TimothyDrake
You key this in as the password and smile. Perfect. Now time to send him a message.
"Who would've thought the Wayne's would be the Batfamily!? - :-)" You type and quickly send.
The look on his face is totally worth it.
The next week you send him messages about others in Gotham. Then one day you send "Do you talk to the Kent's much because I got to say their undercover thing kind of sucks. - :-)" This is just to prove you have full access to their database.
"I spent a whole week on that single code... the password was my name. How insulting." You receive the message from him rather suddenly.
"Insulting? I could have major feelings towards you." You retort.
"Well I hope you don't."
"Man, it must be all the coffee. Seven cups right? You look dead tired" You send a text. The look on his face is priceless. The shock and horror as he looks directly at his camera means he knows you can see him.
"Why are you doing this?" He asks, resuming his more chill and tired expression.
"Hmmm. Just wanted to test my skills, Batman has the best security in the hacker world." You send back. This is partly true, and it was fun.
"We will find you and put you to jail." He threatens. WOW. Putting in jail because I know who they are? Not even asking how you managed this. But you did hack them. Kind of rude. Time for a distraction!
Not even ten minutes later you have a full map of Joker's weapons and arms deals.
"Cool! But here's a map of where the Joker's weapons are at, he's not too good at hiding his footsteps on cyberspace" You send the message then the map.
"How do I know if this is legitimate." He replies quickly. No love loss here.
"Because I'm trying to make you not follow my tracks, gotta throw someone under the bus. See you soon - :-)" You send a message then sign off so you can go to class. The weekend has ended.
The classes are all easy to you, but you need the degree to get a decent job for any company. The week goes by and in the afternoons you send Tim messages. Seems to you that he and the rest of the family appreciates your help, but Tim is annoyed by your existence. He's discovered you have multiple IP Addresses all in Gotham and even asked which one is yous. But no hints are given from you. Not even a code name.
That Friday the professor comes in and says he has exciting news. Strange because this is the most boring man ever.
"Mr. Wayne has announced that his company is holding a competition for who can break his code the fastest. Whoever wins gets a top spot in his IT Department." The professor announces. He then adds, "This is going to the three top colleges in Gotham."
A competition. Really?
I could win something like that so easily. And I will. Talk about easy job grabbing. And they more then likely know it will be.
When home you message Tim, "A competition? Really? You know that I will win."
"That’s the point." He messages back.
"If you wanted to know who I was you could’ve just asked." You say teasingly. He has asked, and you just toyed with him. He's fun to tease. What can you say.
"I think I tried that already." Is the short response he gives to you.
"Oh yeah, huh. Well, see ya tomorrow." I send and sign off.
The next morning you put on the basic winged eyeliner, mascara, and lip balm then put on your "No Talkee Before Coffee" T-shirt, jeans, and vans. You sit down and when the timer starts you begin tapping away. Same system as the batcomputer, so it was no surprise that it only took you an hour to win the competition.
When Tim got up to see who you really were you could see he was shocked. You watched him walk down your isle looking you up and down. You can't help but to smirk small at him. Doubt he expected it to be a girl his age with long (h/c) hair put up into a messy bun.
He gave a nervous gulp as he went up to shake your hand. You could see the gulp as he did it. You politely shook his hand and leaned closer. "Why do you look so nervous Red?“ You jokingly whispered into his ear.
"You… look… not what a worldwide hacker usually looks like.” He stutters out nervously.
You cocked an eyebrow and giggle. You really can't be offended because the poor boy looks like he got hit by a train or something. He's clearly starstruck. "What does that mean?" You ask playfully.
"It means that Tim thinks your hot.” Dick appears behind him and shakes your hand. He has a amused smirk and You giggle as Tim blushes. "Thanks for all the help.“ Dick then adds with a smile before giving Tim a pat on the back and slightly pushing him towards you.
You can't help but to blush a little yourself now.
"Sooo, does the winner get a kiss from the famous Drake?” Dick jokes and looks at you both.
"What? No…. at least not here." Tim stutters at first then recovers as he says this. You blush even more.
"So... I get a kiss instead of jail time..?" You tease softly and this makes Tim blush.
Looks like you got yourself two jobs and a new friend.
#tim drake x reader#tim drake imagine#tim drake headcanon#tim drake#red robin#red robin headcanon#red robin x reader#red robin imagine#batfamily headcanons#batfamily imagine#batfam headcanons#batfamily#batfan#batfam#batfic
98 notes
·
View notes
Text
Lastly, let's talk about Development Choices. And also if you're ready to expand past shared organizing?
In your area organized web sites assure remarkable reliability. So, we approved the challenge of establishing our Server Farm in India location for high-end business companies, naturally, maintaining budget plan in mind. All our information center places are power and network repetitive, encouraging unhindered functioning of web servers, since the day they are activated. Organisation Email is a professional, entry-level email service for every single kind of businesses. Appreciate abundant storage with 5 GB area as well as the capability to access your e-mail on any device. Scripting languages consist of PHP 5.x, Perl, Python. Linux Dedicated Web server Hosting comes with CentOS 6.x. Ubuntu, Oracle Linux are additionally readily available as custom OS options. Dedicated Servers Linux is powered by Intel Xeon Processors, 1 Gbps Port Rate, FREE DirectAdmin Control Board, 4 IPs, Arrowhead Web Server Platform. Linux Dedicated Servers supports OS like CentOS, Ubuntu, Oracle Linux and also with leading control panels like DirectAdmin, Plesk.
What is the cost of organizing a web site in India?
The Internet Hosting A webhosting is actually stores your internet documents. domain name india Organizing is generally an annual charge. At domainindia.org it's $9.49 (Rs.510) each year this strategy as well as space is ample for the typical client. our all web hosting plans is that you can conveniently update to an any type of plan if you must require it.
All Our Netherlands Servers Include.
Choosing the best economical dedicated web servers India offers is a vital choice. You may discover a specialized service to come to be extra economical than you may think, however at the exact same time, it is vital that the company shall be reputable. As there are lots of vendors, that can market you something at the most affordable cost yet later you are mosting likely to face the lack of exceptional service as well as assistance. Yes, we do indeed provide both Self-managed and Completely Took care of servers. Additionally, our industry grade firewall programs and also data safety and security systems aid in nullifying not just malware strikes, however additionally data theft and also leakages. We totally comprehend just how crucial it is for your organisation services to be readily available to your customers, which is why we make certain 99.95% ensured network availability for essential business site( s) & application( s), with full freedom for you to select your preferred information service provider. The cloud has actually become associated easily of operating, especially an information technology based company. Also business that handle conventional services and products are progressively moving their online jobs to the cloud to make sure that their inner sources are maximized to focus on offline tasks. internet For core technical companies, the prevalent fostering of the cloud has given complete web server services to ensure that their services are never ever at risk of being disrupted.
What is the most affordable means to host a website?
I have actually listed a few of the least costly methods to hold your start-up internet site, thinking about cost, system and also service size: Hostwinds. This VPS hosting solution is just one of the most inexpensive host carriers you will have the ability to discover. Bluehost. FatCow. A Small Orange. 1 & 1. GreenGeeks. description Hostgator. InMotion Hosting.
Numerous bandwidth backbones provide a repetitive network accessibility.
Windows Reseller Hosting, you can provide customized Windows Organizing strategies or create sites on ASP/. WEB for your clients.
Motherboard or power supply is regarding to fall short, our specialists will certainly replace it within 4 hours if your difficult disk.
Our internet servers also extend assistance to MySQL, MS SQL data sources in addition to movement assistance and also optional took care of services for Level three as well as Level 4 support.
It is essential that you take into consideration the high cost of a specialized web server as an investment rather than stress over it. For the specialized server cost in India that you are paying, you are getting top quality, reliability, protection, and also performance while providing your visitor a responsive and fast experience. A devoted server is functionally equal to an internal web server, just far more affordable. It is exclusively Dedicated to your demand offering you the control over sources and equipment on lease. Each of our specialized web servers include complimentary DDoS security to make the most of availability & stop unanticipated downtimes from interrupting your organisation as well as revenue stream. With full root accessibility, you have the ability to customize any kind of software program as well as mount that you need to optimize specialized server. For start-ups that are looking for the most basic webhosting strategy, you'll probably only require a single internet site. A web hosting service that supplies just a solitary domain is likewise the most affordable options, yet if you're seeking to add even more internet sites you require to ensure your host can support it. While most host plans enable as several subdomains as you like, you need to make certain they can sustain more domain names if that's what your company demands.
What are dedicated servers utilized for?
A dedicated server is an enterprise-grade physical server made use of to hold the applications and also services of a single hosting client. Dedicated servers are typically made use of to host high-traffic web sites, web applications, and also for other organizing situations where performance is paramount. You have the power to use it for any kind of function. Nobody will certainly be sharing the sources or can trigger any disruption to you like in common organizing. Till a few years back, yes, the specialized web servers were extremely highly priced. Nevertheless, like with several other items, with enhancement in innovation as well as the increase in competition, the committed web server rate in India has boiled down as well as end up being even more cost effective.
Free Plesk Panel.
Our specialized servers utilizes the SuperMicro blade chassis, which has a little footprint with decreased power consumption as well as cooling requirements. These effectiveness enable us to pass price financial savings down to you so your expenses are maintained to a minimum. Our servers are powered by Intel Xeon HyperThreaded processors, DDR3 RAM as well as 7200RPM SATA drives. We use an exclusive provisioning system which ensures that your devoted hosting server prepares promptly. You will certainly have the alternative of selecting in between CentOS, CloudLinux, and the Windows Web Server 2016/2012 OS, with the completeness of our Vint Hillside based Dedicated Web servers. One (1) IP addresses (IPv4) is consisted of with each Dedicated server located within the Vint Hillside. This is given at no added price. You will have the alternative of choosing in between CentOS, CloudLinux, and also the Windows Web Server 2016/2012 OS, with the totality of our United States based Dedicated Web servers. Five (5) IP addresses (IPv4) are consisted of with each Dedicated web server located within the UNITED STATE On top of that, they are easily scalable. If you intend to boost your bandwidth ability, call our support group. Host as numerous sites as you want on our inexpensive dedicated web server. There are many organizing business exist in India, offering hosting at various prices. There are some little affordable web hosting firms that supplies hosting for much cheaper rate, They have the ability to provide for much cheaper rate as a result of poor quality of support & re-selling of various other's hosting. Mainly, You can have a respectable running internet site with the bandwidth supplied in the common organizing. An ordinary price of server comes between Rs 6 to 8 Lacs. Yes, we do offer WHMCS as an invoicing panel for your committed web server. You can purchase the certificate from us at a minimal expense, and after that install it on your committed web server. Our highly resistant information centers and also dedicated web servers are kept an eye on continuous by internal IT staff for ensuring smooth holding experience. On the other hand, in Unmanaged Dedicated Server organizing plan, the customer selects to perform all these tasks by their very own in-house IT specialists. Trying to find least expensive devoted web server hosting plan?
#dedicated server hosting in India#cheapest dedicated server hosting in India#low cost dedicated serv
1 note
·
View note
Text
How to Sideload Apps on Android TV?
Android TVs have turned out to be amazingly famous in the course of the most recent year or somewhere in the vicinity, on account of the developing number of makers offering brilliant TVs crosswise over various value portions. Notwithstanding, there still aren't a ton of applications on the Play Store that are planned in view of the TV interface. In any case, that doesn't mean you can't utilize these applications on your savvy TV. In this way, in case you're searching for approaches to attempt and run your most loved applications on your TV, here's the manner by which to sideload applications on Android TV:
Sideload Apps on Android TV utilizing USB Flash Drive
One of the least demanding approaches to sideload applications on your Android TV is by utilizing a blaze drive. You simply need to duplicate the APK document for the application you need to introduce into the USB streak drive, and afterward plug it into your Android TV. To do this, simply pursue the means given beneath:
On your Mac or PC, download the APK document for the application you need to sideload. You can utilize sites, for example, APKMirror for this. We'll be sideloading "Netflix" for this instructional exercise. When the APK is downloaded, duplicate it into a USB drive.
Attachment the USB crash into the Android TV box, and dispatch ES File Explorer. Here, find the USB drive you connected, and open it.
netflix apk in es record pioneer
Explore to the area where you spared the APK record, and essentially click on it to start introducing it on your Android TV.
es record pilgrim introduce spring up
Certain organizations, for example, Xiaomi likewise add a File Browser to their Android TVs and you can utilize that application simply like ES File Browser to sideload APKs onto your shrewd TV.
xiaomi worked in pilgrim interface
That is fundamentally it. You have now effectively sideloaded Netflix onto your Android TV utilizing a USB drive. On the off chance that, for reasons unknown, you're unfit to utilize a USB drive to sideload applications, you can utilize a FTP server, alongside ES File Explorer, to sideload applications on an Android TV. We'll examine that next.
Sideload Apps on Android TV utilizing FTP
1. Sideload Apps on Android TV utilizing Mac
Sideloading applications on an Android TV is definitely not a troublesome undertaking. All you need is a record pioneer on your Android TV that can interface with FTP servers, and a FTP Server running on your Mac. Both of these can be accomplished effectively. Simply pursue the means beneath:
On your Android TV, dispatch the Play Store, and introduce ES File Explorer.
es document pioneer play store
When done, go to System Preferences on your Mac, and afterward click on "Sharing."
framework inclinations macintosh sharing choices
In the left segment, check "Document Sharing" and "Remote Login" and permit access for "All clients". Here you will something on the lines of "ssh <username>@<ip address>". Observe the username and the IP address of your machine.
empower sharing all clients macintosh
On your Android TV, dispatch ES Explorer, and go to Network - > FTP.
es record pilgrim arrange ftp
Snap on "New", select "sftp", and include the subtleties for your protected FTP server, as pursues:
Server: 172.xx.xx.xx for my situation
Username: tusharmehta for my situation
Secret phrase: The login secret word for your Mac
es document traveler ftp marking in
You would now be able to download APK documents for the applications you need on your Mac, at that point go to the download goal from ES File Explorer, and basically introduce the application from that point.
introduce apks from es ftp
2. Sideload Apps on Android TV utilizing a Windows PC
In case you're utilizing a Windows PC, you should utilize an outsider application for making a FTP server on your PC. The procedure can be somewhat confounded, along these lines, here are every one of the means for straightforwardness:
Download and introduce FileZilla Server (not Filezilla FTP customer) on your PC. Keep in mind the port number you enter amid the establishment. While it is set to 14147 as a matter of course, you can pick any number as long as you remember it. I utilized 10000
Once FileZilla Server is introduced, begin a server by entering localhost in the hostname and the chose port number
Sideload Apps on Android TV
Snap on "Alter", and after that on "Clients"
filezilla alter clients
Go to "Shared Folders", and snap on "Include", under "Clients"
filezilla shared organizers new clients
Enter the username you need the FTP customer to sign in with.
Sideload Apps on Android TV
Next, click on "Include" under "Shared Folders"
filezilla include shared organizers
Select the index you need to share over FTP. I'd prescribe utilizing an organizer explicitly for FTP purposes.
Sideload Apps on Android TV
Snap on "alright" and your FTP server is currently set up.
filezilla make ftp server
Note: You may need to handicap your Firewall in case you're unfit to associate with your FTP server from a similar system.
Next, we have to associate our Android TV, with the FileZilla server on our PC. Essentially pursue the means beneath:
On your Android TV, dispatch ES Explorer, and go to Network - > FTP.
es record wayfarer arrange ftp
Snap on "New", select "ftp", and include the subtleties for your FTP server, as pursues:
Server: The IP address of your PC. You can discover this by running ipconfig in the Command Prompt.
Username: The username you made while setting up the Users in FileZilla.
Secret word: Leave this clear
windows ftp association
On your PC, you can download the APKs, and spare them to the organizer you set up in "Shared Folders" in FileZilla. At that point, essentially open the FTP server in ES File Explorer, and introduce the application from the APK.
permit introduce obscure applications android television
Note: You should permit establishment from "Obscure Sources" on your Android TV, to have the option to sideload applications.
Sideload and Run any Android App on your Android TV
The Android TV Play Store has a deficiency of TV perfect applications. Along these lines, except if you sideload applications on your TV, a ton of incredible applications like Google Chrome, Skype, and Google Drive will be remembered fondly out. While you can introduce practically any Android application on your Android TV by sideloading it, a ton of applications don't carry on appropriately. For instance, you won't almost certainly click on connections in Google Chrome, on the grounds that there's no cursor accessible there. In any case, you can combine a Bluetooth console or USB console, a standard or remote mouse, or an air mouse with your Android TV, and utilize that to explore around the interface.
As usual, we might want to know your contemplations on Android TVs, just as the absence of applications in the TV Play Store.
1 note
·
View note
Text
Printer Security – What To Do?
When taking a gander at big business security, we ordinarily allude to and think about firewalls, Intrusion Prevention Systems (IPS), Virtual Private Networks (VPN), encryption and confirmation. When we consider verifying our information, we consider verifying basic servers and databases. Once in a while do we consider printers. Billions of dollars are spent worldwide on security every year, except what amount did your association spend on verifying their printers this most recent a year? On the off chance that you addressed zero, you would be in by far most.
Printers have made considerable progress since their across the board appropriation in the late 1970's and mid 1980's. Some time ago, every printer was associated with an individual framework and could just process a solitary print work at once. Today, printers have developed into multi-utilitarian gadgets that uncovered little similarity to their inaccessible starting points. Printers in the 21st century perform many undertakings including, yet not restricted to, printing, examining, photocopying, faxing and notwithstanding messaging reports. What most clients, and even framework, system and security directors don't understand is the thing that truly goes on inside a printer and what usefulness they genuinely have. Most clients still think about the printers of 30 years prior; unintelligent gadgets that just have the capacity to print reports. This view is far expelled from reality.
While examining printers in this article, we are not just discussing the behemoths you see in most expansive endeavors, yet in addition your low-end multifunctional printers you presently discover basic in customary family units. Uncommon is it to discover a printer, regardless of how little, that just plays out the single errand of printing. Most, at an extremely least, furnish faxing or examining and with these come expanded memory prerequisites. Checking a full archive in readiness to print, examining a report to be spared as a PDF or comparable record, or filtering a report to permit faxing all require the capacity to support the information inside the gadget. A cushion is fundamentally an area of memory that permits the putting away of transitory information. Printers utilize this cushion to store a computerized form of the report you are printing, examining or faxing. Contingent upon the gadget, this cradle can extend from a little bit of Random Access Memory (RAM) to a Hard Disk Drive like the sort found in your work area or workstation phone. In bigger undertaking printers, this support isn't the main memory store found inside the printer. A bigger, non-unpredictable memory region is given to store semi-changeless or perpetual data. For instance, a few printers permit examining of a report and sparing it inside the printer as a PDF. The client may then associate with the printer as though it were a system drive, or by means of a website page, and download their archive.
So where are we running with this? The spillage or robbery of delicate and classified corporate data. Expansive endeavors may have created and executed information maintenance and devastation strategies yet seldom do these incorporate, or even notice, printers. Organizations take a gander at printed versions of reports, CD's, DVD's and workstation, PC and server hard drives when building up their information devastation strategies. While it is clear they recognize hard drives as a wellspring of touchy data, once in a while do they consider the hard drives contained inside their printers, on the off chance that they even know about their reality. Printers are likewise normally neglected when security strategies, methodology and rules are created and executed. Brief period, assuming any, is spent taking a gander at printer security or the ramifications of not verifying the corporate printers. All the all the more irritating this moves toward becoming when you mull over the regular sorts of archives that go through printers in a professional workplace. Contingent upon the business or the office inside the association, archives can fluctuate from touchy budgetary records, individual client information or point by point organize outlines, to give some examples.
To see how delicate information is spilled through a basic printer to the outside world, it requires a comprehension of the professional workplace, security controls inside that condition, and the general stream of data between clients, printers and record frameworks that house confined information.
In the perfect, secure professional workplace, a client has confined access to records that relate to his or her activity work. The records dwell on a safe server inside the corporate system and are ensured by solid access control approaches requiring a client to verify before being enabled access to documents. In our model, a client requires a touchy monetary record for a gathering he is going to visit. The client confirms to the server, access to the document is approved by the entrance control approaches set on the record and the client opens the document in Microsoft Word. He taps on the print symbol and sends the archive as a print employment to his closest printer. With this basic demonstration, we have taken a safe record that exceptionally constrained clients approach, and have made two duplicates that are never again ensured by any type of access control. The first is the self-evident; the paper duplicate our client requires for their gathering. The second is a duplicate housed in the cradle on the printer. In the perfect world, our client will guard the printed duplicate consistently and pursue the association's information demolition strategy and annihilate the duplicate of the record when they never again require it. With respect to the virtual duplicate made on the printer, the client has no genuine authority over this, nor presumably realizes it even exists. On the off chance that we are fortunate, the record is overwritten when the following print work comes through, yet this is reliant on the brand and model of printer and how the printer was at first set up by the chairman.
In both of these situations, ill-advised transfer of a decommissioned printer could have calamitous ramifications for an organization. Rented printers might be come back to the renting organization for resale. Obtained printers are disposed of in the junk or sold at closeout or online by means of sale destinations, for example, eBay. In any case, innumerable touchy records could go under the control of terrible people. While the spilling of certain archives could monetarily influence associations, releasing individual data relating to hundreds or thousands of clients or customers could have notoriety repercussions that could devastate an organization.
Most associations don't understand the maximum capacity of their printers or the usefulness they have accessible. While much usefulness is non-security related, these capacities have significant effect on the security of the information inside an association and should be comprehended and tended to. These incorporate, however are not constrained to:
1. The capacity to duplicate documents to Windows or Unix SMB record servers
2. The capacity to email filtered records to a client
3. Functionality that enables printers to get faxes and after that forward the fax onto predefined clients by means of numerous strategies, for example, email or as another fax, and
4. The capacity to store records which have been checked, printed, messaged or transferred locally on the printer
While most printers have the capacity to validate both printer heads or ordinary printer clients, most of the time, this usefulness is incapacitated or left in its default state; crippled. Five minutes on Google and an aggressor will probably discover the default secret word to practically any printer. When executive access is picked up to a printer, it takes brief period and even less capacity to make changes to settings that could be disastrous to an association. While it would be little yet irritating to wind up bolted out of your printer, or the interface changed to another dialect so nobody could control the printer, if the assailant was to divert your printing or duplicate reports to an area outside the inward system, contingent upon the substance of the document, it could be the ruin of an association.
So how does an association ensure itself against assaults against printers and spillage of delicate information?
A couple of basic advances:
1. Disable pointless usefulness. In the event that any capacity inside the printer isn't required inside your business, incapacitate it. The less administrations or capacities a printer has running, the less roads of assault or spillage the printer has.
2. Add printers to your information maintenance and transfer approaches. Ensure all memory inside printers is discarded by means of secure demolition or secure cleaning when printers are decommissioned.
3. Ensure information is overwritten following printing. This needs the printer being used to help this usefulness, however in the event that your information is exceedingly delicate, this ought to be a need when taking a gander at new printers.
4. Print from memory as opposed to hard plate drive if accessible.
5.Use the protected printing alternative, if accessible, so printouts don't begin before you achieve the printer and enter your secret key. How frequently have you hit print, strolled to the printer and your printout is not a single where to be seen, just to turn up lying on a table days or even weeks after the fact?
6. Examine where printers are coherently situated inside the system. Printer the board interfaces ought to be limited and just open from characterized the executives IP's. Guarantee printers are never open from the Internet. Evaluate whether a few or all printers ought to be situated inside their own zone of trust.
7. Use the inbuilt security inside the printer to confine who approaches, what get to they have and where they may access from.
Verifying printers ought to be an indispensable piece of verifying your information. Security arrangements should exist that address the dangers and characterize how printers ought to be verified. Create printer security rules and methodology for usage of new printers and pursue these guidelines to guarantee all printers are verified and don't turn into a high hazard to your association. By verifying your printers, you are adding to your by and large layered security demonstrate and ensuring your association's basic information alongside
1 note
·
View note
Text
Configuration tutorial for Hubstudio fingerprint browser and this Proxy agent
Hello, the configuration process for this Proxy proxy is similar to that of 911s5 proxy. It is achieved through multi-port forwarding to connect this Proxy proxy and Hubstudio fingerprint browser. For example, if you want to open 20 Hubstudio fingerprint browser windows simultaneously, this Proxy proxy will configure 20 ports for each window.
To do this, you need to add 20 port forwarding rules in the MaxProxy client, pointing to different ports of the Hubstudio fingerprint browser. Then, configure 20 different network proxies in the Hubstudio fingerprint browser, each corresponding to a MaxProxy proxy forwarding port. In this way, 20 Hubstudio fingerprint browser windows can access the network through the MaxProxy proxy, and each window will have its own network proxy, which will not interfere with each other.
To begin, configure the basic settings for MaxProxy agent.
Note: The MaxProxy proxy download is a compressed package and needs to be extracted before use. If you try to use it directly from the compressed package, it will not work properly.
Choose a different proxy tool,
If MaxProxy and Hubstudio fingerprint browser are on the same computer, it is recommended to select 127.0.0.1 for the listening address (especially when running in a virtual machine or VPS)
If the MaxProxy proxy and Hubstudio fingerprint browser are not on the same computer but are in the same LAN (on the same router), the listening address should be changed to 0.0.0.0 and use the local LAN IP. It is recommended to turn off AP isolation and firewall on both computers.
Finally, remember to click "Save" to apply the changes.
Static IP configuration tutorial:
1.MaxProxy port forwarding configuration: Set a unique IP address for each port.
2.Hubstudio fingerprint browser proxy IP configuration: Set a unique port for each Hubstudio fingerprint browser window.
New Environment - Proxy Settings (Newly created browser: Click the three dots next to the Open button - Modify Proxy)
Proxy type selection: Socks5
Usage Selection: Use according to static IP rules
Agent Host:
If MaxProxy and Hubstudio are on the same computer, it is recommended to select 127.0.0.1 for the listening address (especially 127.0.0.1 is recommended for running in virtual machines or VPS)
If the MaxProxy and Hubstudio are not on the same computer and are in the same LAN (in the same router), the listening address is changed to 0.0.0.0 or the local LAN IP. It is recommended that the router not turn on AP isolation and turn off the firewall for both computers.
Proxy port: For details about how to configure port forwarding, see Local Port Forwarding or LAN Port Forwarding
Agent account and proxy password: leave blank without entering.
Check whether the proxy connection passes.
Finally, finish saving proxy settings.
Dynamic residential IP/dynamic computer room IP configuration tutorial:
Generate the required dynamic IP in the MaxProxy agent software and extract it to each Hubstudio fingerprint browser
Hubstudio fingerprint browser proxy IP configuration: configure a dynamic IP for each Hubstudio fingerprint browser
New Environment - Proxy Settings (Newly created browser: Click the three dots next to the Open button - Modify Proxy)
Proxy type selection: HTTP or Socks5
Usage Selection: Use by dynamic IP rules
To configure the agent host, proxy port, agent account, and proxy password: After copying the dynamic proxy information from the MaxProxy agent software, copy one of the dynamic IPs from the selected MaxProxy agent. Then, in the Hubstudio browser, click on the proxy host input box and use the keyboard shortcut Ctrl+V to paste the proxy information. This is a convenient and efficient method, and it eliminates the risk of typing errors. Verify that the proxy connection is successful and then save the proxy settings.
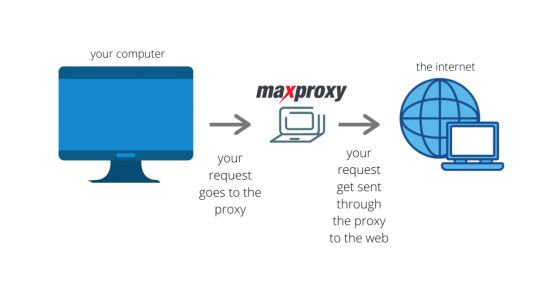
1 note
·
View note